
In our increasingly digital world, data is the new gold. From personal information and financial records to intellectual property and business secrets, vast amounts of sensitive data reside online. This abundance of valuable information attracts a growing breed of criminals: cybercriminals.
Cybersecurity, the practice of protecting systems, networks, and data from unauthorized access, use, disclosure, disruption, modification, or destruction, has become more critical than ever. This blog delves into the importance of cybersecurity, exploring its role in safeguarding data, ensuring business continuity, and navigating the ever-evolving threat landscape.
Table Of Content
What is Cybersecurity?

At its core, cybersecurity revolves around protecting the CIA triad: Confidentiality, Integrity, and Availability.
- Confidentiality ensures that only authorized individuals can access sensitive information.
- Integrity guarantees data and systems remain accurate and unaltered.
- Availability ensures critical systems and resources are accessible when needed.
- By implementing robust cybersecurity measures, businesses and individuals can maintain control over their data and prevent unauthorized access or manipulation.
Why is Cybersecurity So Important?
The importance of cybersecurity transcends simple data protection. Here are some key reasons why businesses and individuals alike must prioritize robust cybersecurity practices:
Protection of Sensitive Data:
- Financial Loss: Data breaches can result in significant financial losses for businesses, covering data recovery costs, regulatory fines, and reputational damage.
- Identity Theft: Stolen personal information can be used for fraudulent activities, causing immense stress and financial hardship for individuals.
- Reputational Damage: A data breach can severely damage a company's reputation, leading to a loss of customer trust and brand loyalty.
Ensuring Business Continuity:
Modern businesses rely heavily on digital systems and infrastructure. A successful cyberattack can disrupt operations, disable critical systems, and lead to significant downtime. This can result in lost productivity, revenue losses, and damage to customer relationships.
Maintaining Compliance with Regulations:
Many industries are subject to data protection regulations such as the Health Insurance Portability and Accountability Act (HIPAA) in the healthcare sector or the General Data Protection Regulation (GDPR) in the European Union. Non-compliance with these regulations can result in hefty fines and legal repercussions.
Safeguarding Online Transactions:
Cybersecurity plays a crucial role in safeguarding e-commerce platforms and financial institutions. Secure online transactions build trust with customers and protect them from fraudulent activities.
The Ever-Evolving Threat Landscape
Cybercriminals are constantly developing new methods to exploit vulnerabilities and gain unauthorized access to valuable data. Here's a glimpse into the ever-evolving threat landscape:
Types of Cyberattacks:
- Malware: Malicious software, including viruses, worms, and Trojan horses, can infiltrate systems, steal data, or disrupt operations.
- Phishing: Deceptive emails or messages attempt to trick users into revealing sensitive information or clicking malicious links.
- Ransomware: This cyber threat encrypts a user's data, rendering it inaccessible until a ransom is paid.
- Zero-day Attacks: These are previously unknown vulnerabilities that exploit software flaws before developers have a chance to patch them.
Increasing Sophistication of Cybercriminals:
Cybercriminals are becoming more sophisticated, employing advanced techniques like social engineering and targeted attacks. These attacks focus on specific individuals or businesses and exploit their unique vulnerabilities.
Benefits of Strong Cybersecurity
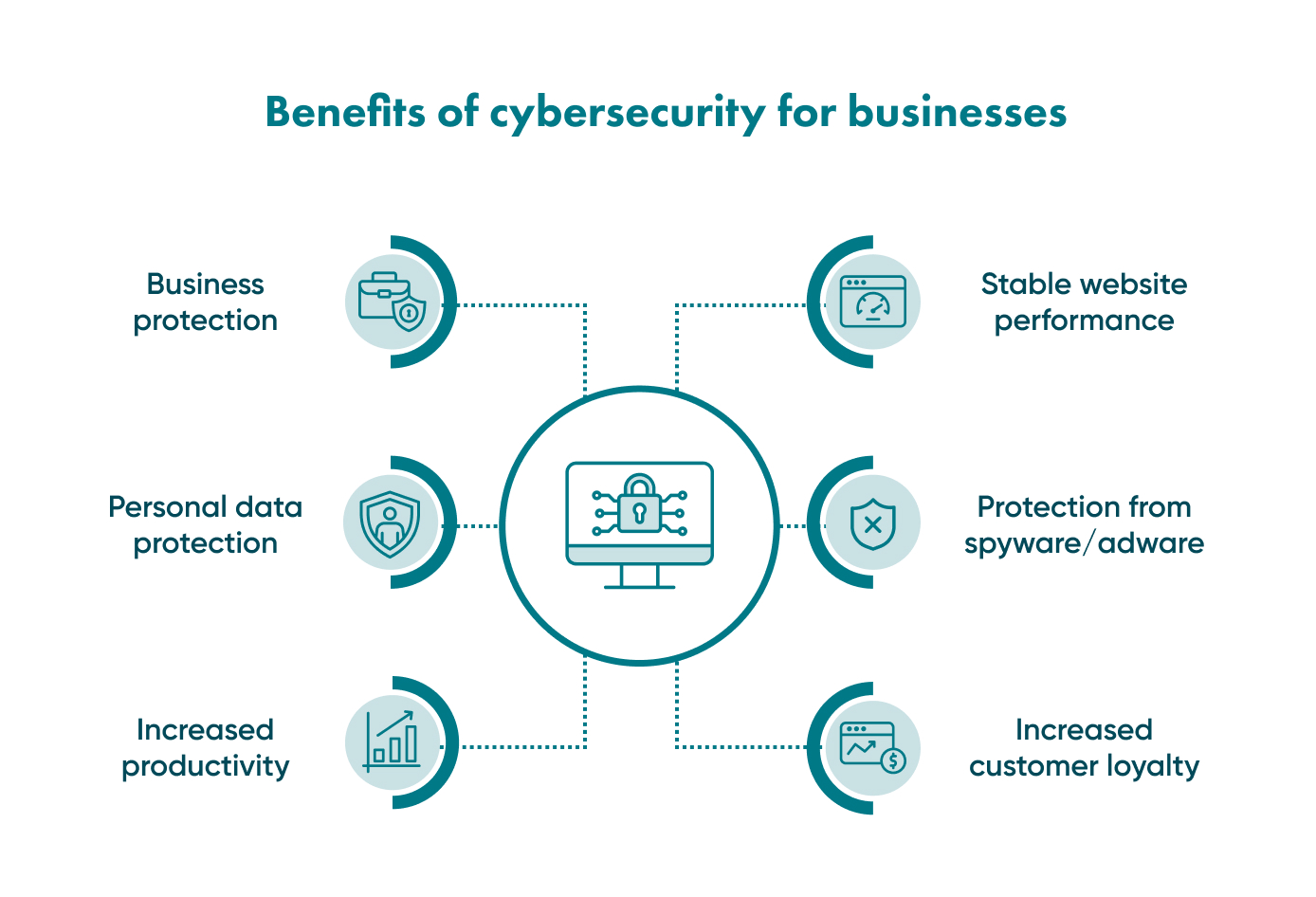
Investing in robust cybersecurity practices yields substantial benefits for businesses and individuals:
- Protects Brand Reputation:
A strong cybersecurity posture safeguards a company's reputation from the damaging effects of data breaches and cyberattacks.
- Saves Money:
By preventing costly attacks and data breaches, businesses can save significant resources.
- Increases Customer Trust and Loyalty:
Customers are more likely to trust and do business with companies that prioritize data security and demonstrate a commitment to cybersecurity.
- Provides a Competitive Advantage:
Strong cybersecurity can differentiate a business from its competitors, especially in industries where data security is paramount.
Best Practices for Businesses and Individuals

Combating cyber threats requires a multi-layered approach. Here are some best practices for businesses and individuals to significantly enhance their cybersecurity posture:
- Implement Strong Passwords:
Encourage the use of complex and unique passwords for all online accounts. Consider password managers to create and manage strong passwords.
- Enable Multi-Factor Authentication (MFA):
MFA adds an extra layer of security by requiring a second verification step, such as a code from a mobile app, in addition to a password for login.
- Install and Update Security Software:
Utilize antivirus, anti-malware, and firewall software to detect and prevent malicious threats. Regularly update this software to ensure it remains effective against emerging threats.
- Educate Employees and Users:
Regular security awareness training for employees can equip them to identify phishing attempts, avoid suspicious links, and report security incidents promptly.
- Maintain Backups:
Regularly back up critical data to a secure offsite location. This ensures data recovery in case of a cyberattack or system failure.
- Patch Management:
Promptly install software updates and security patches to address vulnerabilities and prevent exploitation by cybercriminals.
- Segment Networks:
Segmenting networks can limit the impact of a cyberattack, preventing attackers from gaining access to critical systems if they breach a specific network segment.
- Secure Mobile Devices:
Implement strong password protection and remote wipe capabilities on mobile devices to safeguard data in case of loss or theft.
- Beware of Social Engineering:
Be cautious of unsolicited emails, calls, or messages that pressure you to click on links, download attachments, or disclose personal information.
- Limit Data Sharing:
Only share personal information online when absolutely necessary and be cautious about what information you post on social media platforms.
The Future of Cybersecurity

As technology continues to evolve, so too will the cybersecurity threat landscape. Emerging technologies like artificial intelligence (AI) and the Internet of Things (IoT) will introduce new vulnerabilities that require innovative security solutions.
Here are some key trends shaping the future of cybersecurity:
- The Rise of AI-powered Security:
AI can be utilized to analyze vast amounts of data to detect and respond to cyber threats in real time.
- Focus on Cloud Security:
With the increasing adoption of cloud computing, robust security measures are crucial for protecting data stored in the cloud.
- Cybersecurity for the IoT:
As more devices become interconnected, securing the vast network of IoT devices will be a critical challenge.
Conclusion

Cybersecurity is no longer an afterthought; it's a fundamental requirement for businesses and individuals operating in today's digital world. By prioritizing robust cybersecurity practices, we can safeguard our data, protect our privacy, and ensure the continued success and stability of our digital lives.
Start prioritizing your cybersecurity today! Implement the best practices outlined above and stay informed about the latest threats and trends. Remember, cybersecurity is a shared responsibility. By working together, we can create a more secure digital future for everyone.

